When you operate a multi tenant sending environment compliance is a major portion of your operations, and yet on occasion something can slip by; a malicious user or malicious third party will use your platform to relay unwanted messages through your platform and anti-abuse professionals will begin investigating the source of the unwanted messages. It is in your best interests to make their investigation as easy as possible.
For legitimate senders the anti-abuse community is a friend, not an enemy. Legitimate senders do not want their networks abused, and the anti-abuse community can help those senders identify malicious users and compromised accounts. To help in their efforts, consider their perspective as they perform an investigation.
An abuse investigator is going to look through the headers of a spam or phishing message looking to identify the infrastructure that was used to relay the message, specifically reviewing the Received headers to see what IPs and hostnames are used:
Return-Path: noreply@mydomain.net
X-Original-To: mail@theirdomain.de
Delivered-To: mail@theirdomain.de
Received: from smtp85.iad3a.emailsrvr.com (smtp85.iad3a.emailsrvr.com [173.203.187.85])
by d167.theirdomain.de (Postfix) with ESMTPS id 79EA2376D7A
for mail@theirdomain.de; Wed, 11 Jan 2023 18:24:34 +0100 (CET)
Authentication-Results: d167.theirdomain.de;
spf=none (sender IP is 173.203.187.85) smtp.mailfrom=noreply@mydomain.net smtp.helo=smtp85.iad3a.emailsrvr.com
Looking at the headers above, please be aware that this was just a random header sample and no abuse is implied in connection with the sender, emailsrvr.com. We are just using this as an example of header that may come under review. In this sample we can see that the message was relayed through MTA nodes associated with emailsrvr.com. Additionally, the investigator will look at domains used for DKIM signing, used in click and open tracking, and any other hints that can help them identify the provider used by the malicious user/hacker.
As the investigator turns to the domains identified, let’s say they find your domain in the hostnames for the MTAs that relayed the message; the investigator will visit the domain in question, and what they see can help or hinder their investigation. In many cases ESPs will use a separate domain for their email infrastructure, and on multiple occasions I’ve seen those domains have no working website at the root of the domain, meaning that the investigator won’t be impressed, and will have to find other ways to identify your traffic.
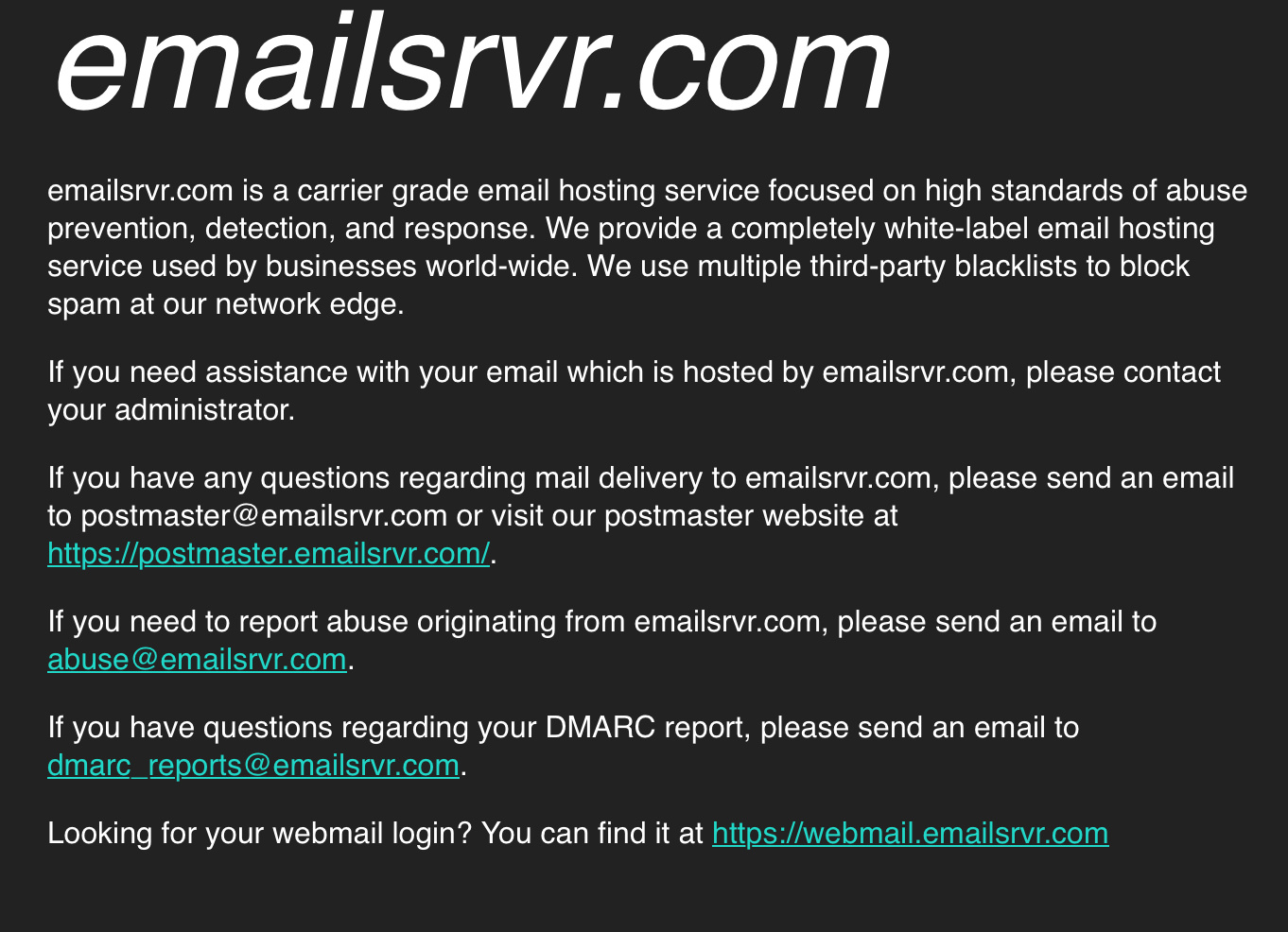
Instead, let’s follow the example of the previously mentioned emailsrvr.com domain. Follow that link, and you’ll see a page like this:

You’ll note that the operators of the emailsrvr.com service are not trying to hide, instead they are doing the right thing by making it clear where to go to learn more about their sending operation, how to contact their team, and how to report abuse.
This is the pattern we want to follow: have a live page available at all domains used by your platform for sending and tracking, with information regarding:
- What the domain/IP is used for.
- Who owns and operates the domain/IP.
- How to contact your team, including an address other than abuse@.
Within their postmaster page the emailsrvr.com operators even maintain a list of the IPs they use for sending (https://postmaster.emailsrvr.com/system-info/sending-ips), something that you may also want to include on your landing page if you don’t maintain a full postmaster page. This allows an investigator to know what other domains and IPs to contact you regarding when doing investigations.
"We operate a spamtrap and one of the main things we do is identifying which operation sent the mail. Doing this is so much easier when the sender is kind enough to provide a list and you don't have to do detective work over a period of time just to get some ideas while still always worried that you probably missed something just because it didn't appear in your data set yet." - Atro Tossavainen, Chief of Operations, Koli-Lõks OÜ, Estonia
A landing page on your infrastructure domains not only help investigators reach you, it’s a good sign to them that you’re interested in identifying and controlling abuse. That said, make sure to respond to abuse complaints in a timely fashion and take meaningful action based on the reports, or that first impression will be lost. Anti-abuse teams would rather work with you to stop abuse, but they will resort to more extreme measures if they need to. It’s better to be alerted and act than to be added to a blocklist.