One of the common requests we get is about examining the message by parts to perform security checks, redact private data, and make technical modifications like adding click tracking to links. The KumoMTA team took this on as part of a wider scope of new features to allow more comprehensive message handling.
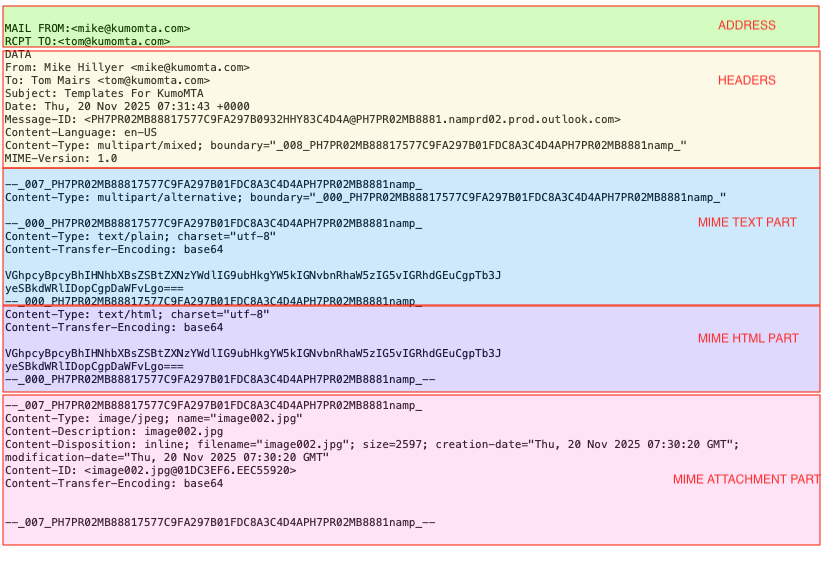
In the last release, kumod 2025.10.06-5ec871ab, we introduced an in-line MIME parser that gives users the ability to decompose a message into its MIME parts. The result of running the 'parse_mime' function on the message object is a table that contains all the separate MIME parts of the message. These can be easily evaluated and modified as strings using the regex and string handling routines we added in earlier releases.
For those unfamiliar, the body of a typical modern email message is composed of several parts that ensure it is consumable by a variety of readers. There is typically a TEXT part, just in case the reader cannot process HTML or attachments. There is usually an HTML part that is what most people actually read. The HTML part includes images, links, and a multitude of font options. There is often a section that contains attachments, and there is room for a number of other formats as well. This is referred to as MIME (Multipurpose Internet Mail Extensions), and you can read the whole RFC here.
Why is this a big deal? With a powerful engine like KumoMTA that can process many millions of messages per hour, it makes some sense to take advantage of that processing power to look after security details, and message enhancements in-line. While our recommendation is to scan and modify messages BEFORE they hit the MTA, sometimes that is unavoidable, or your corporate policies require a "last-mile" verification. KumoMTA functions empower senders to do things they would not be able to do with less capable systems.
For example, there are many companies that handle credit card data, and it is possible that someone's credit card number could potentially end up in an unsecured email. That could be a disaster if the wrong person were to have that information. If a company were using KumoMTA, they could examine the body of every message leaving the server, scan for a pattern that matches a possible credit card number and redact it IN-LINE without involving a third-party tool. If you have over-engineered your deployment and have plenty of spare CPU, you might be able to do this without significantly impacting performance. A few lines of code could save you from a million-dollar lawsuit.
Another common issue is the danger imposed by attachments. Exposing the MIME parts allows an operator to extract the attachments specifically, without affecting the rest of the message. These can be scanned for malware and removed if needed, then the message can be modified to indicate the result if desired.
local subject = mimepart.headers.subject()
subject = subject .. "[MODIFIED] - Attachments were moved to quarantine!"
mimepart.headers:set_subject(subject)
msg:set_data(tostring(mimepart))
There are other reasons to access MIME parts, like ensuring there is a valid TEXT part, because often content creation systems only include the HTML part. You can examine the MIME structure to see if a TEXT part is populated, then modify it if it is not. While you are at it, you can add an open pixel to the top and bottom of the HTML parts for tracking if needed. If you want to go crazy, you can search the whole HTML part for anything that looks like a link and wrap it with your custom click tracker.
What's even better is that it works in both directions. While we typically build features for outbound senders, these functions work equally well for inbound if you are hosting mailboxes or processing security for a mailbox provider. We encourage you to try it out.
Let us know if this helped you - we would love to be part of your story.
------------------------------------------------------------------
KumoMTA is the first open-source MTA designed from the ground up for the world's largest commercial senders. We are fueled by Professional Services and Sponsorship revenue.
Join the Discord | Review the Docs | Read the Blog | Grab the Code | Support the team